
The power sector has experienced rapid digital transformation, significantly optimising productivity across the power value chain and allowing the industry to navigate the increasing complexities of modern power systems. However, amid this exciting change, a new kind of pressure is building: a surge of cyberattacks that energy leaders say is outpacing the sector’s cybersecurity readiness.
Shubbhronil Roy, VP of digital grids strategy and transformation at Schneider Electric, tells Power Technology that cybersecurity is one of the three defining themes shaping the grid today: “Cyber threats have more than doubled in the past two years, and grids are being targeted. Disrupting the grid can plunge entire cities into darkness, making this a critical issue.”
A recent survey, conducted by Power Technology’s parent company, GlobalData, reveals mounting anxiety across the sector as cyber threats multiply, from vulnerable supply chains to new AI-driven threats.
Download sample pages of selected reports
Explore a selection of report samples we have handpicked for you. Get a preview of the insights inside. Download your free copy today.
What emerges from the survey, circulated among power industry professionals, is a portrait of a sector both aware of its vulnerabilities and struggling to close the gaps.
How prepared are power companies? A sector split on confidence
When asked about the extent to which their organisation had implemented and maintained cybersecurity measures, responses varied sharply, revealing a fragmented landscape of readiness: 36% said their organisation has fully implemented and regularly tested cybersecurity measures; 23% have implemented comprehensive measures but do not test them consistently; 19% have only partially implemented; 13% have plans but haven’t started; and 9% have no plans at all.
“Our businesses need to remain smart,” said Abbie Badcock-Broe, head of corporate strategy at National Grid, at the Future of Utilities Smart Energy conference last week. “That means that not only should we continue investing into different forms of cybersecurity but also that implemented measures are maintained, tested and all that becomes just standard practice over a long period of time.”
Confidence in recovery from cyberattacks was equally uneven, with 19% of respondents reporting they were “very confident” in their organisation’s ability to detect, contain and recover from an attack. The majority were either “neutral” (27%) or “somewhat confident” (27%), while the remaining were “not very confident” (15%) or “not confident at all” (12%).
For Erin Illman, partner and chair of the energy cybersecurity and privacy team at Bradley Arant Boult Cummings, this discrepancy points to a larger issue: the sector still treats cybersecurity as a technical bolt-on rather than a core strategic function.
“To address cyber threats, companies in the power sector must shift from a purely technical or compliance-driven approach to a strategic, business-level posture,” she says. “Cybersecurity should be integrated into enterprise risk management and treated as a core business continuity issue.
“Scenario planning and stress testing is imperative to help leadership understand the real impact of potential disruptions and justify investments in controls, redundancies and resilience measures. Board engagement is equally vital – boards must be equipped to understand the threat landscape and oversee cybersecurity as a strategic risk on par with financial, operational and regulatory risks.”
Supply chain most vulnerable to cyberattacks
Asked to rank the most vulnerable areas of the power ecosystem, respondents put supply chain and third-party vendors at the top.
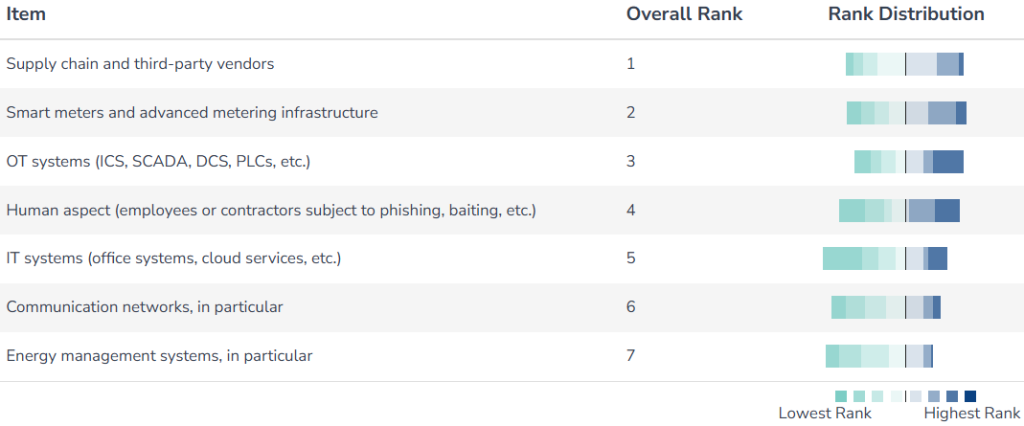
“Across the power sector, the greatest cyber risk sits in the software supply chain and the third-party components woven through both IT [information technology] and OT [operational technology] environments,” Joe Saunders, CEO of critical infrastructure cybersecurity service provider RunSafe Security, tells Power Technology.
According to a 2024 report on cybersecurity in the energy sector, nearly half (45%) of cybersecurity breaches at energy companies in the US originated from third-party vendors, while the global recorded rate was 29%. Among third-party breaches, 67% were due to software and IT vendors.
“The industry relies heavily on embedded software inside controllers, sensors and grid management devices, and any inherited vulnerability in those components from suppliers can silently propagate across critical systems,” Saunders explains. “Without visibility into the provenance and hardening of that code, utilities are exposed to exploits that can be reused across multiple sites.”
He warns that malicious actors are exploiting software vulnerabilities to gain access to devices and map the power grid, just as they mapped telecom networks earlier this year. “Gaining access to devices allows adversaries to answer questions like: What are the peak demand times? Which distributed energy resources (DERs) are most relied upon? If energy software isn’t secured, devices become quiet sensors feeding adversaries the metadata they need to understand where the grid is vulnerable and how to disrupt it.”
Smart meters and advanced metering infrastructure followed closely among respondents’ rankings, with OT and IT systems and human error (such as ‘phishing’ and ‘baiting’) not far behind.
According to a 2024 study, the most vulnerable areas in smart meter infrastructure include distributor servers, linkages, the remote management network and the network hub.
Meanwhile, experts agree that OT and IT systems have become increasingly more vulnerable to cyberattacks due to the increase in integration between the two. While IT/OT convergence is integral for seamless operations in the digital age, it “widens the attack surface” for malicious actors, Illman cautions.
As companies converge their systems, Roy recommends a hybrid cloud model: “Less critical applications can run in the cloud; mission-critical ones can stay on-premises. This combines agility and security.”
When asked which emerging cyber risks most concern them in the years ahead, respondents again pointed to supply chain attacks.
Close behind were threats to DERs, which have seen rapid expansion in recent years, creating more entry points for attackers. GlobalData analyst Alfie King notes: “The management and operation of these assets require automation, which introduces information exchanges between the DER and an energy company’s distribution control system to manage the flow of energy in the grid – and the technologies that enable this communication can lack security.”
AI-driven attacks ranked third, with Saunders noting that “AI now enables attackers to produce exploits faster than operators can patch them.”
“The emergence of AI-driven malware and the long-term risk posed by quantum computing add new layers of complexity to the power sector’s cybersecurity requirements,” Illman adds.
Although geopolitical hybrid threats ranked further down the list, Saunders argues that they have the potential to become “the most concerning risks for the power sector over the next five years”, given recent developments that demonstrated energy systems being increasingly targeted amid rising geopolitical tensions.
Building cyber resilience
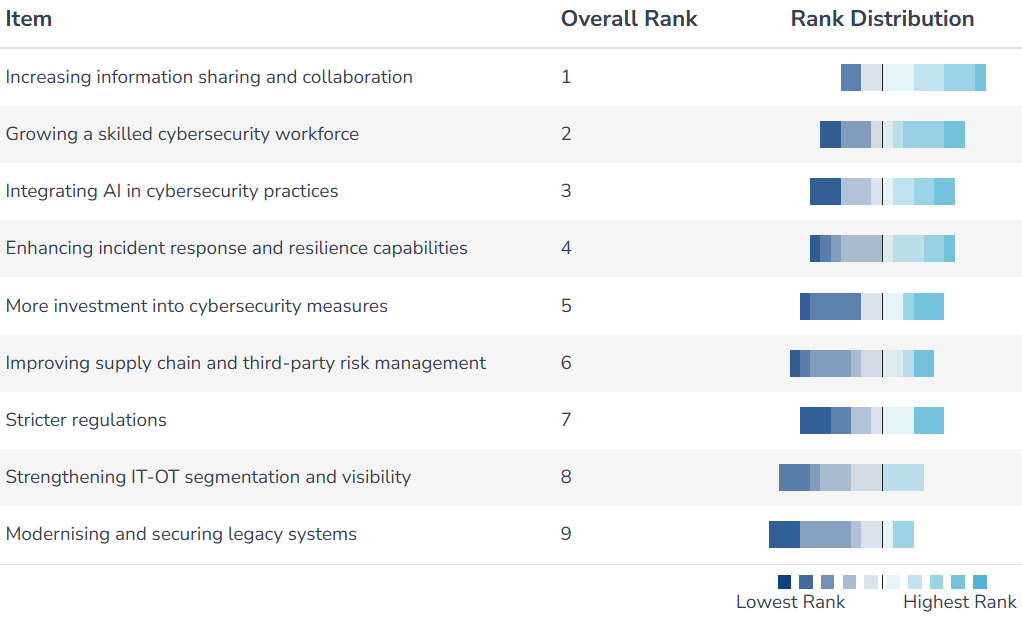
Asked what the sector must prioritise going forward, “increased information sharing and collaboration” came first. Indeed, industry and regulator groups such as ENISA and the ECCC have been rolling out initiatives to facilitate real-time information sharing and coordinate responses both domestically and internationally.
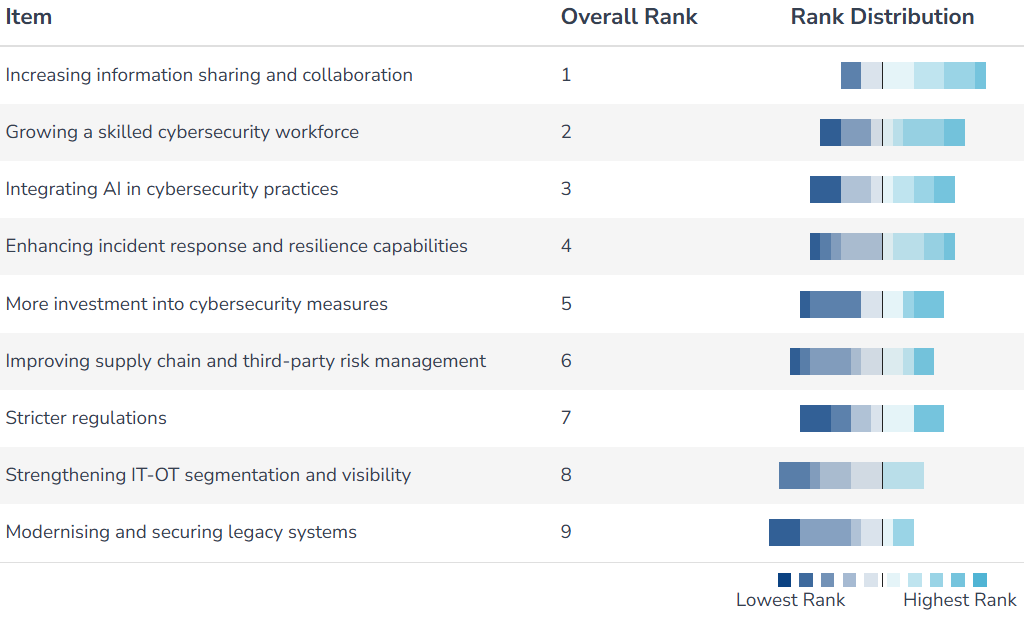
Second was “growing a skilled cybersecurity workforce”– a persistent challenge as the sector competes with tech giants for digital talent.
Lucy Webb, head of people partnering at So Energy, says the key to the energy industry attracting a digitally skilled workforce is “connecting to purpose”. “It is about ensuring that they know they are not just doing a tech job – they can be really pivotal in the evolution of the energy sector and climate change. The job they are signing up for can create a brighter future for everyone.”
Beyond recruitment, Illman highlights developing digital skill sets internally as being of equal importance. “A strong organisational culture, including a security-aware workforce, reduces the likelihood of social-engineering failures and operational missteps,” she says, adding: “Encouraging cross-department collaboration ensures that engineers, operators, IT professionals and executives share a common understanding of risks and resilience priorities.”
Integrating AI into cybersecurity practices also ranked highly among respondents. “To counter new AI-driven cyberattacks, we also need to use AI and other security protections to create an asymmetric shift in defence, giving operators the upper hand even as threat actors move more quickly,” says Saunders.
Illman summarises: “In an era defined by AI and looming quantum disruption, a culture of vigilance, adaptability and shared responsibility is one of the most powerful defences the power sector can cultivate.”
That means even priorities that ranked lower remain crucial, and industry must work together to develop cybersecurity on all fronts.
“We cannot afford cyberattacks and disruption to the energy systems that underpin our technological and economic progress,” Saunders concludes.
Unlock up to 35% savings on GlobalData reports
Use the code at checkout in the report store
-
20% OFF
Buy 2 reports
Use code:
Bundle20
-
25% OFF
Buy 3 reports
Use code:
Bundle25
-
30% OFF
Buy 4 reports
Use code:
Bundle30
-
35% OFF
Buy 5+ reports
Use code:
Bundle35
Valid on all reports priced $995 and above. Cannot be combined with other offers.
Still deciding what will work best for your business?
Ask our experts for help.
Enquire before buying



